Why do we need network security?
Let’s answer this question first. Organizations use network security to prevent any malicious use or accidental damage to a network’s private data.
It helps to reduce the risk of falling victim to data theft and sabotage.
It even protects the workstations from spyware that is too harmful ensuring the security of shared data.
Table of Contents
Top Ways to Achieve Network Security

img source: sectigostore.com
We can adopt several ways to help achieve network security. Some of the recommended ones are:
- Using strong authentication methods.
- Upgrading software with the latest security patch.
- Establishing cybersecurity rules for your employees and making them aware of good security practices.
- Enabling data encryption and requiring the users to enable bios passwords.
- Equipping all the devices with antivirus and anti-malware protection.
- Ensuring your network is using a secured Virtual Private Network (VPN) to create secure Internet connections to and from your private networks.
- Performing regular security audits at least on an annual basis.
Out of all the above means to ensure network security, using a Virtual Private Network (VPN) is greatly preferred among the users.
Let’s understand what a VPN is and how it helps to boost network security.
What is a VPN?
- VPN is a mechanism that employs encryption, authentication, and integrity protection so that the users can use a public network as if it’s a private network.
- VPN offers a high amount of security and allows its users to remotely access a private network. It simulates a private network over a public network.
- You can choose from the best VPNs for 2024 as suggested by CoolTechZone.
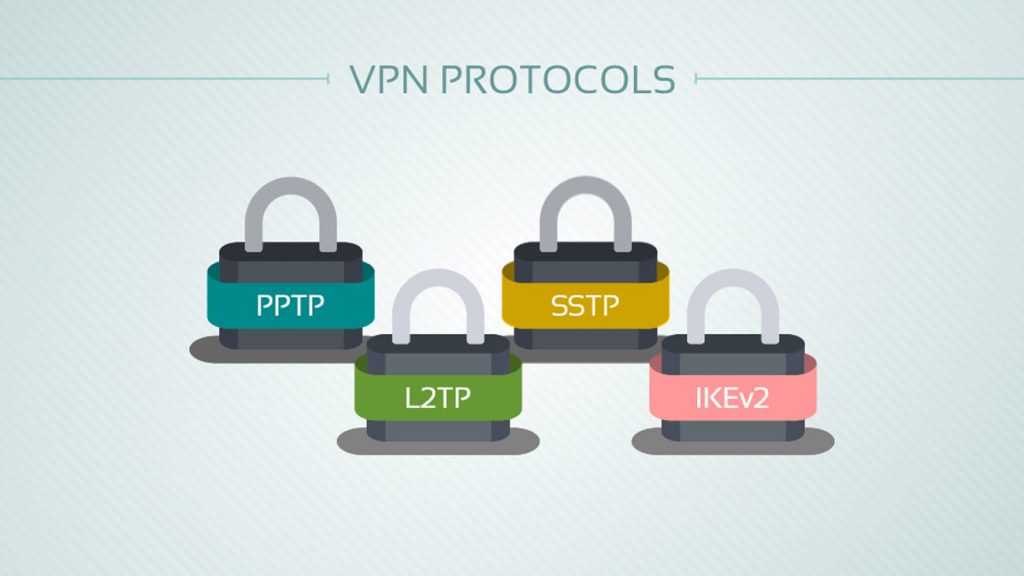
There are two different modes or protocols for implementing VPN:
img source: www.privacyend.com
- Point to Point Tunneling Protocol (PPTP)
- Layer 2 Tunneling Protocol (L2TP)
Point to Point Tunneling Protocol is a basic security protocol that is used for VPN normally on Windows NT systems whereas the Layer 2 Tunneling Protocol is an advanced version of Point to Point Tunneling Protocol.
PPTP supports connectivity between a user and a Local Area Network (LAN) whereas L2TP supports connectivity between both users to LAN and LAN to LAN.
Types of VPN
There are two major types of VPN as discussed below:
1. Remote Access VPN
Through this, the users can connect to a private network and remotely access its services and resources.
It is used by home users or private users to bypass the regional restrictions on the internet and access blocked websites.
2. Site-to-Site VPN
It is also known as Router-to-Router VPN and it is mostly used by corporates.
This type of VPN consists of two routers where one acts as a VPN Client and the other as a VPN Server. The Site-to-Site VPN is of two types:
- When a Site-to-Site VPN is used to connect the remote offices of the same company, it is called an Intranet-based VPN.
- When a Site-to-Site VPN is used to connect the offices of two different companies, it is called an Extranet-based VPN.
Points To Keep in Mind While Choosing a VPN

img source: medium.com
Before you choose any top VPN, It is important to keep the following points in mind:
- It is important to figure out what you need in a VPN. For example, if you want a VPN for your entire household, a router-based VPN is what you should look for. Else, if you are planning on streaming movies online then you need a VPN with high speed, reliable connections, and unlimited bandwidth.
- Look at the qualities of VPNs such as speed, encryption, anonymity, etc.
- Checking which devices are compatible. Some VPNs are not available on all platforms.
- It is important to find a VPN with a user-friendly interface.
- If you are choosing a VPN for business purposes then choose the one that provides reliable customer service and comes with a money-back guarantee.
It is best to compare the best VPN services available (especially their individual features) in the market before you select any of them for your needs.
Securing Your Network Using a VPN
Now that you have understood what is a VPN and how to choose the best one.
Let us look at some important tips you need to follow to help secure your network using a VPN.
- Use the strongest possible authentication method for VPN access- This depends on the network infrastructure, for example, If there is a network with Microsoft servers then the Extensible Authentication Protocol-Transport Level Security (EAP-TLS) provides the most secure authentication by using smart cards.
- Use the strongest possible encryption method for VPN access- As discussed earlier, Layer 2 Tunneling Protocol (L2TP) is more advanced and should be used over Point to Point Protocol (PPTP) and Internet Protocol Security (IPsec) unless your client passwords are guaranteed to be strong.
- Limiting VPN access to those with a valid business reason and only using a VPN when it is required- Remote employees should be discouraged from using VPNs to check their emails or download commonly needed files.
Apart from the tips discussed above, there are many other ways to secure your VPN .
Final Thoughts
Businesses have now upgraded to new and better technologies to use in networks, which improves the features of existing VPNs. Over the years, the VPN-specific technologies haven’t changed much because the current VPNs do a great job to keep businesses connected around the world. Use a VPN to boost the security of your network and keep your personal or business data safe. You can visit consumerchoice.com and check out the Top VPN Services provider you will want to use. Make sure to choose that VPN thaw will help your business to mask your identity while browsing through the internet, protect your online privacy, and maintain your data security.







