Domain names are considered newly registered within a few weeks from the time they were added to the Domain Name System (DNS) or changed owners. That would be about 30 days from the time the domain name was registered. Hundreds of thousands of them are registered per day, which translates to millions of NRDs every week or month. They span several purposes.
New businesses need to register domain names to compete with other companies in their respective markets. Established organizations may also need to register other domain names for their new ventures. These and many more are legitimate and helpful use cases of NRDs. But this post looks at the dark side of NRDs. How are cybercriminals using them? Should companies trust NRDs? Should they be blocked from corporate networks?
Table of Contents
3 Ways Threat Actors Abuse Newly Registered Domains
Here are three common ways that NRDs are used maliciously. It’s important to emphasize that NRDs are only a part of a threat actor’s arsenal. They could also use old domain names to execute malicious activities.
Typosquatting Domains in Phishing Campaigns

Source: ebrandservices.com
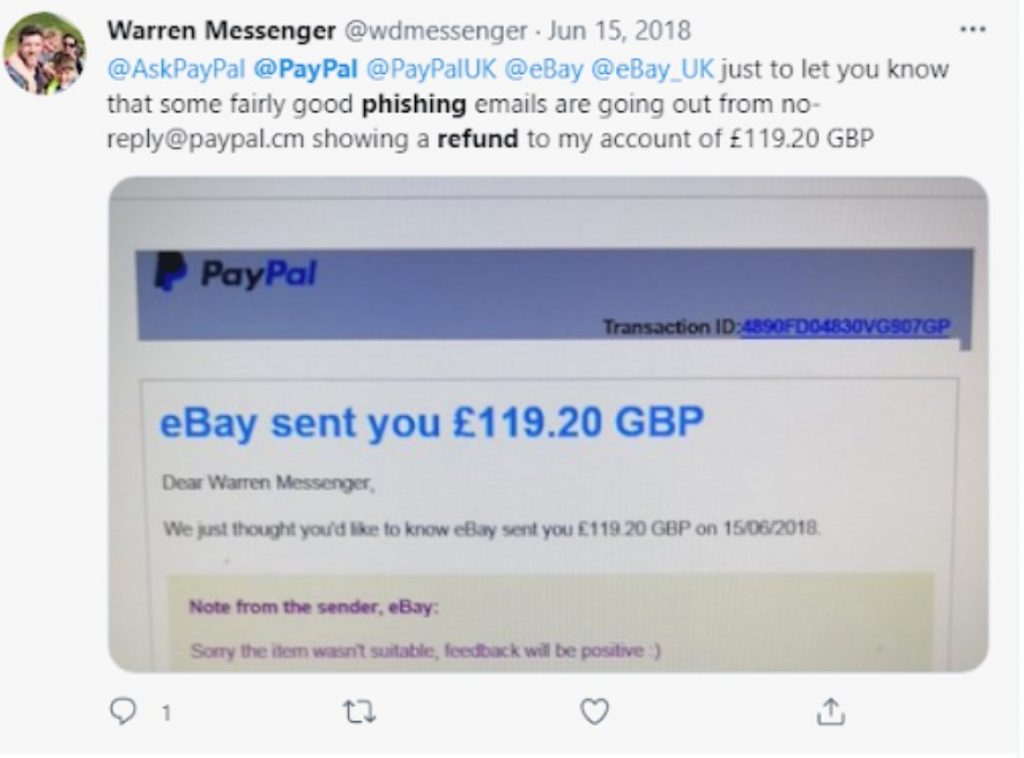
Phishing is a type of cyber attack where bad guys impersonate a trusted person or organization. To accomplish this, they usually use domains that imitate the official websites of the target entity. We call these typosquatting domains, as they are often misspelled variations of legitimate domains.
Aside from misspellings, they may also use other text strings and top-level domains (TLDs). Some examples of typosquatting domains are:
- amazon–amazonjp[.]co
- jp-amazon-amazon[.]top
- microsoftmagi[.]com
- onlinemicrosoft[.]nl
- exn2paypal[.]com
If you run these on blocklist sites or threat intelligence platforms, you would find that they have been reported as malicious. And they are not the only ones. Studies that looked at newly registered and added domains and subdomains related to some of the most impersonated brands found that a high percentage of them gets flagged as malicious.
Threat actors can use typosquatting domains to send phishing emails similar to this email a Twitter user received:
Machine-Generated Domains in Malware Attacks
Machine-generated domains comprise random alphanumeric characters and are usually created using domain generation algorithms (DGAs). Below are a few examples of DGA-manufactured domain names:
- nzwygkp[.]cn
- xzwljby[.]cn
- mkqiqnqhqklwnqa[.]club
- poajeuchbveuw[.]club
- 360kt-43c54sx[.]cn
- 360kt-94kpf2[.]cn
These types are often seen communicating with the command-and-control (C&C) servers of malware families. By using DGA, attackers can easily switch from one domain to another, thus avoiding detection and blocking. Considering that a single DGA-powered malware can generate as many as 50,000 domain names per day, it would be quite difficult for security teams to pin down the C&C server. As such, DGA-generated domain name detection is crucial to protect your network from malware.
News-Related Domains in Misinformation Campaigns

Source: businessblogshub.com
Current events have been known to affect domain name registration trends. Some of them can be used in malicious activities, including phishing and other scams and misinformation campaigns. Below are some examples of news and current events that spurred a wave of domain name registrations in the past year:
- Black Lives Matter: Based on our research more than 1,000 NRDs were seen between 26 May and 15 June 2024, days after the unfortunate death of George Floyd that sparked civil unrest and the global Black Lives Matter movement. The domains contained strings, such as “George,” “lackliv,” “loyd,” and “alli.”
- COVID-19 pandemic: COVID-19-related domains keep appearing in NRD feeds such as this one, which notably peaked around the time the World Health Organization (WHO) declared it a pandemic. Between January and March 2024 alone, about 55,000 coronavirus-related domains were registered.
- 2020 U.S. elections: Spikes in election-related domain registration were detected around the time of presidential caucuses and primaries. Most of them contain the names of presidential candidates.
- COVID-19 vaccine: The volume of domains containing the word “vaccine” spiked in December 2024, when some countries began their vaccination campaigns. The trend was also detected a day after President Vladimir Putin announced the approval of Sputnik.
While some of these news-related domains may be harmless, some may be used by threat actors. In fact, coronavirus-themed domains have been seen hosting misinformation and phishing content. WHO even had to release warnings about COVID-19-related scams.
Top TLDs Used in Newly Registered Domains
In the first half of 2024, a majority of the total domain name registrations fell under the .tk (11%) and .com (10%) TLDs. This finding is similar to the domain registration trend for July 2024, when 1,048,576 NRDs were found.
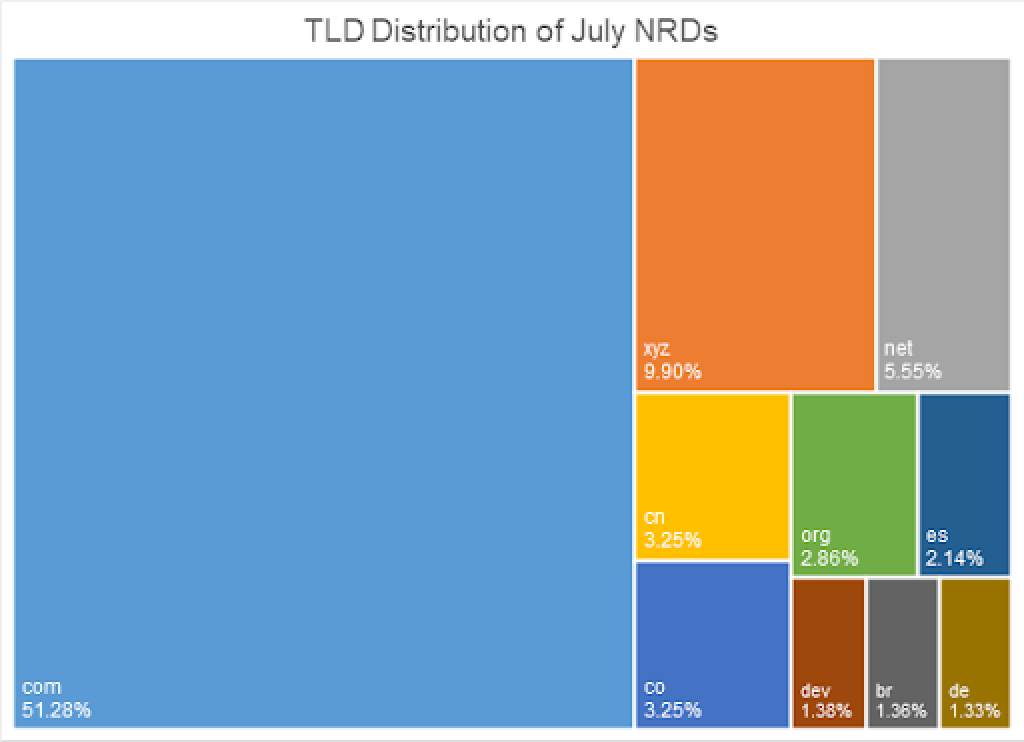
When we downloaded the Newly Registered Domains Data Feed for the July, we found that more than half (51.28%) of the NRDs used the .com TLD, followed by .xyz (9.90%), .net (5.55%), .cn (3.25%), and .co (3.25%). On the other hand, the .tk TLD was used by only 0.35% of the NRDs. The TLD didn’t make it to the top 10 TLDs used in NRDs registered in July 2024, as shown by the chart below.
Should Companies Block Newly Registered Domains?
Several cybersecurity experts are proponents of blocking NRDs. In 2019, Palo Alto Networks recommended that traffic to and from NRDs be blocked or monitored closely. Other experts suggest blocking NRDs for at least 15 days since malicious domains could be dropped or reported around this time. When deciding whether to block NRDs or not, the key is to weigh the chances of false positives against the risks they pose. The decision could depend on the industry you’re in.
For instance, it would be more beneficial for banks and financial institutions to block NRDs. After all, these organizations mainly deal with highly specialized and established entities that are less likely to use NRDs. However, allowing NRDs in their network would expose them to risks of unquantifiable data breaches and data theft.
Organizations in the IT industry, on the other hand, could miss out on potential clients if they block NRDs. New companies with new domains may be interested in their services. In this case, scrutinizing and monitoring NRDs would be the best option.
NRDs are used in both legitimate and malicious activities, as illustrated in this post. As such, the decision to block them or not isn’t as straightforward as we would want. At the very least, monitoring NRDs and investigating suspicious ones would benefit organizations in any industry.